CoinDCX $44 million hack: inside the breach and the urgent role for forensic investigations

July 31, 2025
In mid‑July 2025, CoinDCX, one of India's largest cryptocurrency exchanges operated by Neblio Technologies, became the victim of a $44 million hack. According to Bengaluru police and internal investigations, attackers gained unauthorized access by compromising the credentials of a software engineer, Rahul Agarwal, via his company‑issued laptop. At around 2:37 am on July 19, a single USDT was transferred out; within hours, the intruders drained $44 million, distributing funds across six wallets.
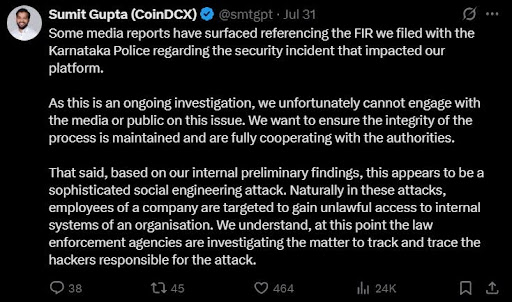
CoinDCX described the incident as a "sophisticated social engineering attack" orchestrated by an actor posing as a recruiter, tricking Agarwal into installing malware on his device. Bengaluru police subsequently detained Agarwal, who consistently denied direct involvement in the theft, although admitting to freelance work for up to four external clients while still employed at CoinDCX. A suspicious deposit of roughly ₹15 lakh (~$18,000) into his personal account and an alleged WhatsApp call linked to Germany remain under scrutiny.
Source: X /@Smtgpt
Why forensic investigations are indispensable in such cases
-
Deep system and endpoint forensic analysis
It is essential to conduct a full forensic examination of the compromised laptop and server logs to trace malware installation, lateral movements, and unauthorized sessions. Such analysis is fundamental to distinguishing between insider culpability and remote exploitation.
-
On‑chain tracing and fund flow reconstruction
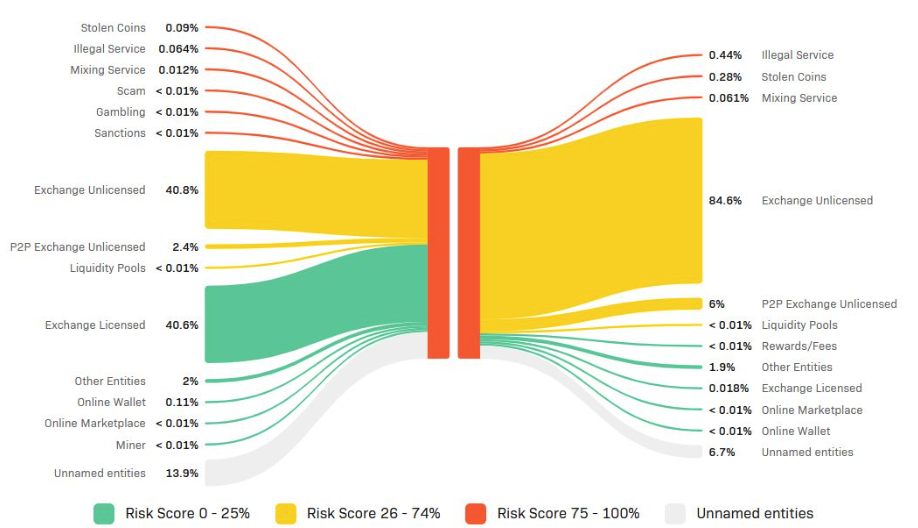
Advanced blockchain intelligence tools are vital to map the movement of funds across chains and exchanges. For example, platforms like Crystal Intelligence or TRM Labs aid investigators in piecing together how stolen assets traverse multiple wallets and obfuscation layers (Figure 1).
-
Chain of custody and legal admissibility
Maintaining an auditable chain of custody is non‑negotiable. Modern forensic frameworks—especially those integrating blockchain-based evidence management—ensure integrity and transparency in legal proceedings.
-
Cross‑jurisdiction coordination
Given that crypto transactions can span borders, forensic labs must collaborate with law enforcement in multiple countries to trace origins, identify beneficiaries, and freeze assets.
Hard Constraints, Not Hopes: The Programmable Custody Stack
- Account-abstraction wallets (ERC-4337) with policy-first design: passkey login → mint scoped session key → policy engine enforces who/what/where/how much.
- Device and context attestation at sign and at send (FIDO/WebAuthn, OS integrity). If posture fails, txn can't be constructed—no 'approve later' loopholes.
- Withdrawal-class segmentation: separate smart accounts (hot ops, warm treasury, cold vault), each with different policy ceilings and approval graphs.
- Live forensic hooks: every policy decision, signature, and session-key grant logged on-chain/off-chain for immediate investigation.
- Destination controls: whitelists, chain/asset allow-lists, time-locks on first-seen addresses; velocity + anomaly caps at the wallet layer.
These preemptive processes and post-event frameworks are paramount to providing an initial shield for customers' funds, as well as a quick response due to time sensitivity, which can prevent bigger losses in these cases. Ensuring coordination and cooperation from exchanges and law enforcement agencies on a national or global scale is equally as important, as these frameworks can serve as the foundations for catching fraudsters and identifying breaches in time to prevent them.
This was underlined by comments in July by Arthur Firstov, Chief Business Officer at Mercuryo—a payment service provider that enables users to buy cryptocurrencies using fiat currency via various payment methods— who said that CoinDCX didn't just suffer a $44M breach; it hit the limits of a non-programmable custody model. He went further to comment that "The fix isn't more training—it's wallet infrastructure that enforces policy by default."
Exchanges keep losing to social engineering because their wallets don't speak policy. Move the control plane into the wallet—via ERC-4337 smart accounts, passkeys, and scoped session keys—and your 'last mile' is code, not a compromised laptop. Privy's reach and Stripe's backing show this is going mainstream; Porto's policy model shows how to do it right. After CoinDCX, treating forensics and policy as infrastructure—not incident response—should be table stakes.
Selecting the right partner for crypto‑forensic resilience
In situations like the CoinDCX hack, timely and rigorous forensic engagement is the linchpin to uncovering attack chains and recovering assets. That's where Blockchain investigators and law enforcement come in. Offering high‑fidelity endpoint investigations, blockchain fund tracing, and legal‑compliant chain‑of‑custody frameworks, investigation experts and dedicated agents bridge the technical and evidentiary gaps in complex cryptocurrency breach cases.
Ondology Labs' insights: Broader implications for the industry
- Strengthened employee risk mitigation: Exchanges must enforce stricter access controls, regular security training, and monitoring to counter sophisticated social engineering.
- Regulatory pressure ahead: As high‑profile hacks accumulate, jurisdictions worldwide are likely to tighten oversight on crypto‑asset custodians and mandate forensic readiness.
- Reputation and trust resilience: Rapid engagement of reputable forensic experts post‑incident helps restore confidence among users and stakeholders.
Reminiscent of the recent major Bybit hack, which featured social engineering as well as the use of mixing, the CoinDCX breach illustrates the dual threats of insider access exploitation and orchestrated social engineering. As investigations continue, only comprehensive digital and blockchain forensic work can clarify responsibility, track fund flows, and support asset recovery. For exchanges, legal teams, and enterprises navigating such crises, turning to a forensic partner can be the decisive step from chaos to clarity.